[ad_1]

Getty Images
One of the world’s most active ransomware groups has taken an unusual—if not unprecedented—tactic to pressure one of its victims to pay up: reporting the victim to the US Securities and Exchange Commission.
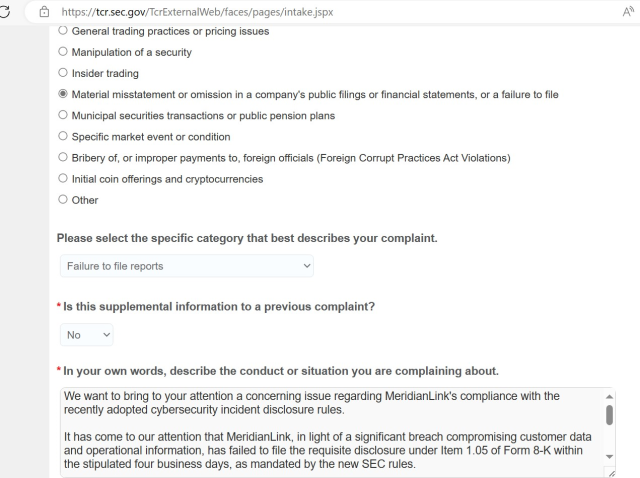
The pressure tactic came to light in a post published on Wednesday on the dark web site run by AlphV, a ransomware crime syndicate that’s been in operation for two years. After first claiming to have breached the network of the publicly traded digital lending company MeridianLink, AlphV officials posted a screenshot of a complaint it said it filed with the SEC through the agency’s website. Under a recently adopted rule that goes into effect next month, publicly traded companies must file an SEC disclosure within four days of learning of a security incident that had a “material” impact on their business.
“We want to bring to your attention a concerning issue regarding MeridianLink’s compliance with the recently adopted cybersecurity incident disclosure rules,” AlphV officials wrote in the complaint. “It has come to our attention that MeridianLink, in light of a significant breach compromising customer data and operational information, has failed to file the requisite disclosure under item 1.05 of form 8-K within the stipulated four business days, as mandated by the new SEC rules.”
The violation category selected in the online report was “Material misstatement or omission in a company’s filings or financial statements or a failure to file.”
Wednesday’s dark web post also included what appeared to be an automatic response received from the SEC acknowledging receipt of the complaint.
As noted, the rule hasn’t yet gone into effect, so even if the breach meets the legal definition of a material event, it’s not likely MeridianLink would be in violation. That said, AlphV is likely capitalizing on the industry-wide anxiety caused by the SEC’s recent decision to sue the chief information security officer of SolarWinds. The SEC alleged the SolarWinds executive misled investors about the company’s cybersecurity practices before a 2020 cyberattack by Russian hackers who then went on to infect 18,000 SolarWinds customers with malware.
MeridianLink officials declined a request for an interview or to answer questions asking if customer data was breached in a network intrusion or whether a security attack took place that could be considered material. Instead, the company issued a statement that confirmed officials had identified a “cybersecurity incident” and went on to say:
Upon discovery, we acted immediately to contain the threat and engaged a team of third-party experts to investigate the incident. Based on our investigation to date, we have identified no evidence of unauthorized access to our production platforms, and the incident has caused minimal business interruption. If we determine that any consumer personal information was involved in this incident, we will provide notifications, as required by law.
Brett Callow, a security analyst with Emsisoft, noted that a ransomware group known as Maze has previously warned victims that it “keeps the communication with the major Securities and Financial Regulators and will acknowledge them on all data leaks and breaches if the agreement is not reached.”
“I’m not sure whether they ever actually did,” Callow told Ars. “Gangs have also threatened GDPR complaints and, IIRC, one may have actually followed through on that.” He said he’s unaware of any group filing a complaint with the SEC. GDPR is short for the General Data Protection Regulation, a European Union law granting individuals broad privacy protections.
AlphV first appeared in November 2021 and is notable for its use of ransomware, named BlackCat, that’s developed in the Rust scripting language. The group targets both Windows and Linux environments.
“As of April 2023, ALPHV has evolved itself into one of the most prolific ransomware groups in the current threat landscape, only falling behind the Lockbit ransomware group in observed activity,” geopolitical and cybersecurity analyst Chris Lucas wrote in May. “Being primarily a Russia-based group, ALPHV will unlikely target organizations based in the Russian Federation or among the rest of the Commonwealth of Independent States (CIS) that make up the former Soviet Union.”
The group was already known for the uncommon practice of threatening to launch distributed denial-of-service attacks on the targets it had already compromised in an attempt to apply extra pressure to pay up.
In trading on Thursday, MeridianLink shares fell 0.2 percent, or 4 cents, to $18.51.
[ad_2]
Source link